Software security is mission-critical in protecting data, IP, and operations from cyber threats. The software infrastructure of an organization serves as an access point to valuable data, intellectual property, services, and tools that are essential for core operations and maintaining a competitive edge. A breach in computer security of these systems can have consequences.
This article aims to guide digital leaders and technology decision-makers in strengthening the security of their software against the growing risks posed by cyber threats. We will discuss strategies for assessing your risk landscape, implementing multiple layers of defense, leveraging advanced technologies, ensuring compliance with regulations, and preparing comprehensive incident response plans.
Given the evolving tactics employed by cybercriminals, no organization must become complacent. By following these practices you can reinforce your security measures against emerging threats targeted at your software foundation. Empower your technology teams to stay ahead of the game.

How to Protect Your Software from Cyber Threats
Conducting a Thorough Risk Assessment: The Basis of Software Security
Cyber threats ransomware attacks are becoming increasingly sophisticated each day. According to IBM’s Cost of a Data Breach Report, 2023 breaches now cost companies an average of $4.35 million. It’s considered the highest recorded in the report’s 18-year history.
With hackers innovating their approaches organizations cannot afford to overlook software risk and security issues in 2025. It is crucial to have visibility into vulnerabilities, employ layered defenses, foster vigilant employees, leverage cutting-edge technologies, and establish an incident response plan.
Performing an evaluation of potential security risks beforehand is crucial to identify any vulnerabilities in your software infrastructure. It’s important to make this a regular practice rather than just a one-time activity.
Identifying Technical and Operational Vulnerabilities
To identify operational vulnerabilities it is recommended to conduct comprehensive penetration testing at least once a year. By hiring hackers you can analyze your software architecture, source code, networks, endpoints, and web applications from an attacker’s perspective. This helps uncover any gaps such as insecure data storage, inadequate authentication methods, exposed interfaces, unpatched systems, and more.
When looking at cybersecurity risks, it’s important to consider both external technical threats as well as vulnerabilities in day-to-day operations. According to Verizon’s 2022 report on data breaches, the main types of cyber attacks come from hacking and social engineering.
Some key stats from the report:
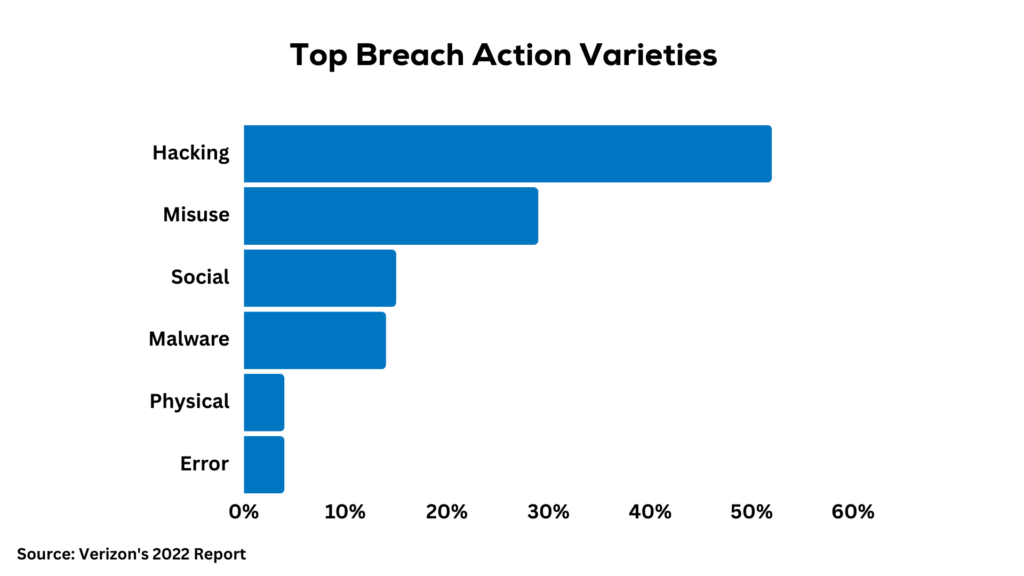
- Over 50% of data breach incidents are caused by hacking – attackers exploiting technical vulnerabilities to break in.
- 15% of breaches involve social engineering – manipulating employees through phishing or other tricks.
- 29% are due to internal misuse – employees misusing data intentionally or accidentally.
These numbers show that companies need strong technical defenses to keep out hackers looking for any system vulnerabilities and weaknesses. But they also need to train employees in cybersecurity awareness. With social attacks and internal misuse common, staff should know how to spot risky emails, questionable links, malicious code, and unauthorized data access.
Additionally, supplement these efforts with infrastructure evaluations carried out by your IT teams. They should focus on identifying human vulnerabilities within the organization. Review policies, processes, and controls related to software application security management to identify any areas of misalignment or non-compliance.
Prioritizing and Remediating Threats
Once the risk assessment is complete it’s important to catalog and prioritize vulnerabilities based on their impact on systems and data and the ease of exploitation. Use a risk matrix that categorizes threats from moderate to severe/critical.
For priority and critical threats identified create clear plans for remediation with assigned owners and target resolution dates. If the fixes are complex, in nature consider breaking them down into incremental steps. It is also important to integrate remediation efforts into your software development lifecycle by obtaining sign-offs before releasing updates or versions.
Third-Party Risk Management
To ensure the security and compliance of your software systems it is important to expand your assessments to include third-party vendors and software users who have access to or integrate with your system. Keep an eye on their security measures and adherence to regulations by utilizing questionnaires conducting audits and thoroughly reviewing their control environments. Hold these vendors accountable by establishing obligations and providing incentives for compliance.
Implementing a Layered Security Strategy
To ensure security it is important to adopt the principle of defense in depth. This means implementing layers of protective measures throughout your software infrastructure. By doing even if software security is important one layer fails there are other safeguards in place to thwart potential attacks. Let’s see, what are the 4 basics of security? When putting together your cybersecurity defense, it helps to keep these 4 main pillars in mind:
- Confidentiality: This means protecting sensitive information through encryption, access controls, data masking, etc. You want to implement security, to make sure the right people can gain access to the data and others can’t.
- Integrity: This pillar is about safeguarding the accuracy of data and system functions against malicious attacks and unauthorized changes. Methods like input validation, hashes, and blockchain help maintain integrity.
- Availability: You want to ensure authorized users can reliably access systems and data when needed. Redundancy, disaster recovery plans, and DDoS mitigation help with availability.
- Accountability: The ability to trace actions back to specific users or entities.
Accountability comes from logging, audit trails, access controls, etc.
Looking at these 4 foundational principles helps you figure out the blend of controls and safeguards needed for your particular systems and risks. The pillars most critical for your landscape should get priority in your security approach. Evaluating against confidentiality, integrity, availability, and accountability gives you sightlines to build effective, balanced defense layers.
Assessment Type | Frequency | Priority Risk Identified | Remediation Plan | Risk Rating | Owner |
External penetration testing | Annual | SQL injection flaws | Input validation controls | High | App Dev Manager |
Internal infrastructure audits | Quarterly | Unpatched web servers | Patch servers, migrate to a new OS | Medium | IT Operations |
Code audits | Per major release | Improper access controls | Role-based access, MFA | Low | InfoSec Analyst |
Third-party risk assessments | Annual | Unauthorized third-party access | Review vendor contracts and security controls | High | Procurement Manager |
Cloud configuration audits | Quarterly | Overly permissive IAM | Tighten IAM policies | Medium | Cloud Architect |
Physical security audits | Bi-annual | Weak door access controls | Upgrade badge reader system | Low | Facilities Manager |
Social engineering tests | Annual | Staff phishing susceptibility | Security awareness training | High | InfoSec Analyst |
DDoS simulation | Quarterly | Network flooding | Tune DDoS mitigation rules | Medium | Network Engineer |
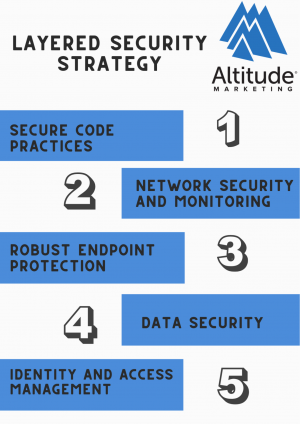
I. Secure Code Practices
How do you make software secure? One crucial aspect is incorporating coding practices into your software development process and lifecycle. This includes adhering to standards like OWASP Top 10 and regularly analyzing code for vulnerabilities using dynamic analysis tools such as SAST and DAST.
It is also essential to enforce design principles, validate input effectively, and perform threat modeling. Additionally fostering a culture of security among developers through training and accountability is vital.
II. Network Security and Monitoring
Employing firewalls, and intrusion prevention/detection systems (IPS/IDS) leveraging threat intelligence feeds and utilizing network access control software security tools allow for connections only.
Monitoring network traffic for anomalies and malicious patterns using solutions like Security Information Event Management (SIEM) can help detect threats. Furthermore segregating systems into secure network segments adds an extra layer of protection.
III. Robust Endpoint Protection
Ensuring endpoint protection is also critical to cloud security. This involves implementing antivirus software, endpoint detection and response (EDR) solutions, patch management tools well as password managers across all endpoints within your cloud infrastructure. Restricting endpoint access through the principle of privilege further enhances security.
IV. Data Security
Encrypting data at rest and in transit while managing data encryption and keys helps safeguard sensitive information. Controlling access to data with role-based permissions ensures that authorized individuals can view or modify it. Additionally masking data whenever possible minimizes the risk of exposure or misuse of sensitive data. Deploying data loss prevention mechanisms along with database audit monitoring capabilities further strengthens data security.
V. Identity And Access Management
Enforcing factor authentication significantly enhances the security posture—particularly for administrative accounts or remote access scenarios. Integrating identity providers is crucial to maintaining consistent access controls across different environments. It is important to review and recertify access privileges while promptly disabling inactive accounts.
The Human Element: Cultivating a Culture of Security
While technical measures serve as the line of defense it is equally essential to involve people in the security equation. Promoting a shared value of security should not be limited to the IT team alone.
Training Employees on Security Measures
Conduct cybersecurity awareness training tailored to various employee roles. Educate them on recognizing engineering warning signs, practicing safe web usage, maintaining strong passwords, and handling data responsibly. Constantly update training materials to address emerging threats and evaluate effectiveness through phishing exercises.
Empowering Developers
Provide secure software development teams with coding knowledge through workshops, cheat sheets, and incentive programs. It is important that software security types and measures do not impede agility but embrace appropriate guardrails. Celebrate those who prioritize secure coding practices.
Promoting Vigilance Across the Organization
Encourage all teams within the organization to take responsibility for security matters. Establish reporting channels for reporting suspicious activities and incentivize individuals who discover some common security flaws and vulnerabilities through responsible disclosure programs.
Vendor Security Practices
Enforce stringent security requirements, in partner, contractor, and vendor agreements. Verify their security training, programs, and access controls while limiting system integration to necessary components.
Leveraging Advanced Technologies
Cutting-edge tools such as intelligence (AI) and blockchain present great opportunities to enhance your security measures. It is important to identify use cases that align with your needs.
Harnessing the Power of AI and Machine Learning
Utilizing the AI tool’s ability to recognize patterns you can effectively analyze behaviors, detect anomalies, identify bot traffic, and mitigate malware threats. The continuous improvement of threat intelligence and detection accuracy is made possible through machine learning.
For example, Amazon uses AI and machine learning in really smart ways across so many parts of its business. In their warehouses, AI helps Amazon manage its supply chain super efficiently. Robots and algorithms let them optimize storage, picking routes, packing, and shipping items in a way that would be extremely difficult for people to manage manually.
Exploring the Benefits of Blockchain
The decentralized nature of technology makes it extremely difficult for transactions to be tampered with ensuring inherent integrity. Consider use cases where blockchain can secure critical software functions transaction records, credentials readable data, and configurations.
For example, banks are using blockchain to improve how they process international payments. Before, when money needed to be sent overseas, it could take days for the transaction to go through and settle. But now some banks are handling international transfers using blockchain technology. This allows the payments to be completed in just seconds!
Instead of taking days, the money can be sent and received almost instantly. International money transfers are almost instant now thanks to blockchain!
Automating Manual Processes
Streamline manual tasks such as patching, log reviews, and report generation by leveraging technologies like PowerShell scripting, robotic process automation (RPA), and security orchestration workflows. This approach significantly improves efficiency and maintains consistency.
For example, supply chain and logistics companies are using clever automated systems these days to optimize their warehouse operations. Rather than relying on manual processes, they’ve implemented inventory management software programs and order fulfillment systems that use algorithms to optimize storage, picking, packing, and shipping.
These automated technologies allow them to track inventory in real time, efficiently route orders for picking, and ensure optimal packing for shipping. This removes a lot of the guesswork and potential for human error. This has led to reduced operational costs and improved customer service by getting orders delivered faster and more accurately.
Ensuring Regulatory Compliance
Maintaining alignment between your software security controls and evolving industry regulations is crucial for your business.
Tracking Compliance Requirements
Keep an up-to-date inventory of regulations such as PCI DSS, HIPAA, SOX, and GDPR based on the specific security software you use along with associated data infrastructure in various jurisdictions. Stay vigilant for any regulatory guidelines or changes to existing ones.
Conducting Regular Audits
Schedule internal audits as well as engage third-party auditors to ensure ongoing compliance, with software security controls. Ensure that any gaps or deviations from policies are promptly identified for remediation.
Automating Compliance Checks
Implement automated compliance checks throughout your development pipelines, infrastructure as code, security monitoring, and testing tools whenever possible. This will provide efficiency and consistency in verifying controls.
Incident Response Planning and Testing
Test your incident response procedures to minimize the impact of potential threats.
Developing Incident Response Playbooks
Test incident response playbooks that outline roles, responsibilities, communication protocols, escalation paths, and appropriate response actions based on likely incident scenarios. Customize these playbooks using threat intelligence specific to your company. Integrate both external response teams into defined workflows.
Incident Response Training and Simulations
Train your teams on incident response through exercises and red team drills to evaluate the effectiveness of your playbooks across different scenarios. These exercises will help identify any gaps in the plans, improve responses, and establish muscle memory through practice. Incorporate the lessons learned from these exercises into revisions of the playbooks.
Post-Incident Analysis
Conduct post-incident analyses after each simulated incident to evaluate what worked well and identify areas for improvement in your response plan and processes. Continuously evolve ongoing processes based on insights gained from these incident reports.
By taking an approach with robust controls in place and tested responses, you can effectively protect your software against emerging threats on the horizon. Encourage vigilance and shared responsibility among all teams involved.
To effectively mitigate cyber risks, it is crucial to prioritize key elements. These include conducting risk assessments, implementing layered defenses, leveraging advanced technologies, ensuring regulatory compliance, and preparing a strong incident response plan.
FAQs
How can we balance software innovation speed with security requirements?
To strike the balance between software innovation and security needs it is recommended to integrate security efforts into existing development cycles. This can be achieved through code training employing threat modeling techniques and adopting test automation practices. Additionally, promoting collaboration between development and security teams helps embed measures while maintaining agility.
What are some oversights that jeopardize software security?
There are common pitfalls that can compromise software security. These include overlooking vulnerabilities, neglecting to patch systems regularly inadequate access controls, and relying solely on single-factor authentication. To see security vulnerability and avoid complacency in this regard it is important to verify the effectiveness of implemented controls.
How long do clients stay with Altitude?
The decision of whether to establish an in-house information security team or outsource to a vendor depends on factors. Smaller companies may find outsourcing cost-efficient as it provides access to specialized skills. Conversely, larger firms often benefit from aligning in-house experts with their technology stack and specific business needs. Evaluating your capabilities will help determine the most suitable approach.
Conclusion
Given the increasing sophistication of cyber threats today businesses centered around software cannot afford reactive or isolated approaches to security anymore. Protecting digital assets requires robust risk assessments, layered defense mechanisms, and cutting-edge technology adoption while adhering to regulatory requirements.
Simultaneously being equipped with well-tested incident response capabilities is essential for quick mitigation when necessary. Cultivating a culture of vigilance and a proactive approach towards all security breaches and incidents further enhances overall protection. By implementing tactics your company can preserve its resilience in the face of changing threats.
Ready to elevate your B2B marketing?
We help leading business-to-business brands hit their marketing goals. Get in touch to learn how Altitude Marketing can help you reach your peak performance.




